Introduction: Viruses and Malware

Computer malware and viruses are terms we’ve all heard of before but what do they mean? What different types are there? And how do you protect against each of them? In the next series of blogs, we’re going to look at the most common types of viruses and how they can infect your system, and […]
The Cloud: What is it and how is it used?

Whilst cloud computing may sound mysterious and confusing, it’s actually a really simple concept. In today’s blog, we’re going to look at what the cloud is and how it can be used at home and in your business. What is the cloud? Simply put the cloud is when you access information that is not stored […]
Bluescreens: What are they and what causes them?
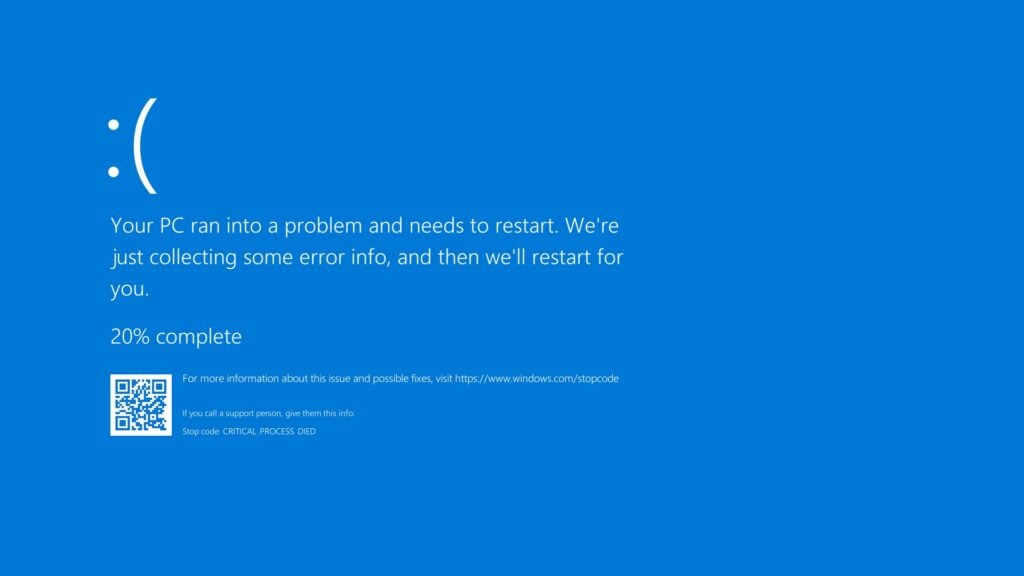
If you have ever spent any time using a computer, you may be familiar with the term ‘Blue Screen of Death’ (BSOD) and you might have even seen a few of them. ‘Blue Screen of Death’ is a light-hearted term for a ‘stop code’, which gives information detailing why a computer crashed. The Blue Screen […]
Managed EDR: The Best Protection

Cybersecurity used to mean download some antivirus software and that was that – easy. But every year we see new threats that use previously unseen techniques to access your data. Your classic antivirus can’t keep up with that. That’s where EDR (or endpoint detection and response) comes in. EDR is the cutting edge of anti-virus […]
Firewalls and Your Business: What and Why?

You may have heard about firewalls at some point but, unlike anti-virus, the name doesn’t really explain what it does. Firewalls are a really important element of your home and business IT security. Today we’re going to look at what firewalls are, how they work and why they are such an important element of your […]
Password Security: How can you keep your accounts secure?

Passwords are normally the one thing standing between you and hackers who are after your data. We often hear the phrases ‘strong’ or ‘weak’ password but what is it that makes a password secure? How do hackers guess passwords? And, most importantly, how can we ensure our passwords will protect us? Today we’re going to […]
